Resource Owner Password Credentials Flow
The Password grant is used when the application exchanges the user’s username and password for an access token. This is exactly the thing OAuth was created to prevent in the first place, so you should never allow third-party apps to use this grant.
A common use for this grant type is to enable password logins for your service’s own apps. Users won’t be surprised to log in to the service’s website or native application using their username and password, but third-party apps should never be allowed to ask the user for their password.
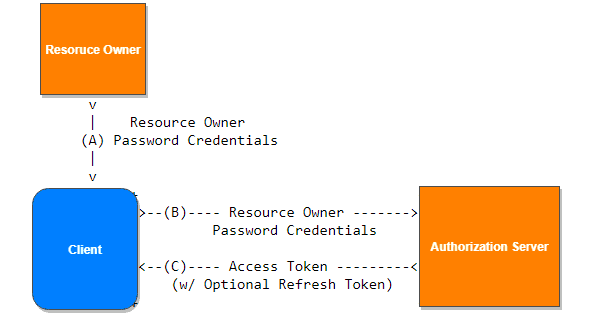
The resource owner provides the client with its username and password.
The client requests an access token from the authorization server's token endpoint by including the credentials received from the resource owner. When making the request, the client authenticates with the authorization server.
The authorization server authenticates the client and validates the resource owner credentials, and if valid, issues an access token.
Request Parameters
The access token request will contain the following parameters.
grant_type (required): The grant_type parameter must be set to “password”.
username (required): The user’s username.
password (required): The user’s password.
scope (optional): The scope requested by the application.
Client Authentication (required if the client was issued a secret)
If the client was issued a secret, then the client must authenticate this request. Typically the service will allow either additional request parameters client_id and client_secret, or accept the client ID and secret in the HTTP Basic auth header.
Example
The following is an example password grant the service would receive.
POST /token-srv/token HTTP/1.1 Host: grant_type=password &[email protected] &password=1234password &client_id=xxxxxxxxxx &client_secret=xxxxxxxxxx &scope=profile address
For example, a successful token response may look like the following:
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"sub": "b2f0bf7d-d060-4014-a90c-f3d9b6b8ade3",
"token_type": "Bearer",
"expires_in": 86400,
"access_token": "eyJhbGciOiJSUzI1******",
"id_token": "eyJhbGciOiJSUzI1NiIs******"
}